The Future of Enterprise Cloud in 2026: Security, Compliance, and Performance Benchmarks
Section
Table of Contents
- The State of Enterprise Cloud Adoption and Security
- Cloud Misconfiguration: The Leading Cause of Cloud Breaches
- Meeting Cloud Security Compliance Standards
- Cloud-Native Security Challenges (Containers, DevOps, and More)
- Hybrid Cloud Strategy: Balancing Security Across Private and Public Clouds
- Multi-Cloud Strategy: Managing Security in a Multi-Provider Environment
- Don’t Forget Performance: Security and Cloud Performance Benchmarks
- Conclusion: Building a Secure and Agile Cloud Future
- FAQs (Frequently Asked Question)
- Practical methods to reduce cloud misconfiguration and identity risk across multi-cloud strategy and hybrid cloud strategy environments.
- A clear set of Cloud Performance Benchmarks: latency SLOs, resilience targets, and unit economics for business-critical and AI workloads.
- Guidance to map cloud security compliance standards into technical controls, evidence collection, and audit-ready reporting.
- An operating model using platform engineering and cloud posture management to scale Enterprise Cloud Security with consistent enterprise cloud solutions.
Enterprise cloud computing has become the backbone of modern business IT, with organizations migrating core systems and data to cloud platforms at record rates. Nearly every large enterprise now relies on cloud services in some form—a recent survey found over 94% of organizations with over 1,000 employees use cloud infrastructure in their operations. idespread adoption brings tremendous agility and scalability. However, it also introduces new security challenges that are top-of-mind for technical leaders. When asked about cloud risks, 88% of government IT agencies cited cloud misconfiguration as a top security concern, highlighting how a simple setup mistake can expose sensitive data., highlighting how a simple setup mistake can expose sensitive data.
Today’s CIOs and CTOs must ensure their cloud strategies keep data protected without sacrificing performance or compliance. This means addressing cloud-native security challenges, aligning with cloud security compliance standards, and managing complex hybrid cloud and multi-cloud strategy deployments, all while maintaining enterprise cloud security across the board. In this blog, we break down the biggest cloud security challenges enterprises face and outline pragmatic strategies (with supporting data) to overcome them.
The State of Enterprise Cloud Adoption and Security
Enterprise adoption of cloud is nearly ubiquitous and often involves multiple cloud platforms. Analysts predict this trend will only grow—Gartner forecasts ~90% of organizations will use a hybrid cloud approach by 2027. At the same time, using multiple public cloud providers has become mainstream. According to Flexera’s cloud survey, 89% of organizations already use a multi-cloud strategy across different providers. In practice, this often means a company might run applications on AWS, store data on Azure, and leverage Google Cloud’s analytics, for example.
This multi-cloud and hybrid cloud strategy delivers flexibility and avoids vendor lock-in, but it comes with added complexity. Each platform has its own security controls, monitoring tools, and best practices. Maintaining consistent security and compliance across all environments is challenging—54% of IT professionals report difficulties maintaining uniform security compliance across hybrid and multi-cloud environments. Integrating these diverse systems is another hurdle: approximately 49% of organizations find it challenging to integrate new cloud services into their existing legacy systems.
Moreover, the scale of enterprise cloud environments is huge. Companies routinely manage hundreds of applications and services across clouds. In fact, studies show enterprises manage an average of nearly 900 different applications across their multiple cloud environments. With such a broad footprint, it’s no surprise that 96% of organizations are concerned about managing security risks at cloud scale. Security teams are inundated with alerts and face skills shortages; about 76% report a shortage of skilled cybersecurity professionals, which strains the ability to secure complex cloud deployments.
Secure cloud. Prove results faster
Cloud Misconfiguration: The Leading Cause of Cloud Breaches
One of the stark realities of cloud security is that many incidents stem from customer-side mistakes, not cloud provider failures. This underscores how critical proper configuration and management are in cloud environments.
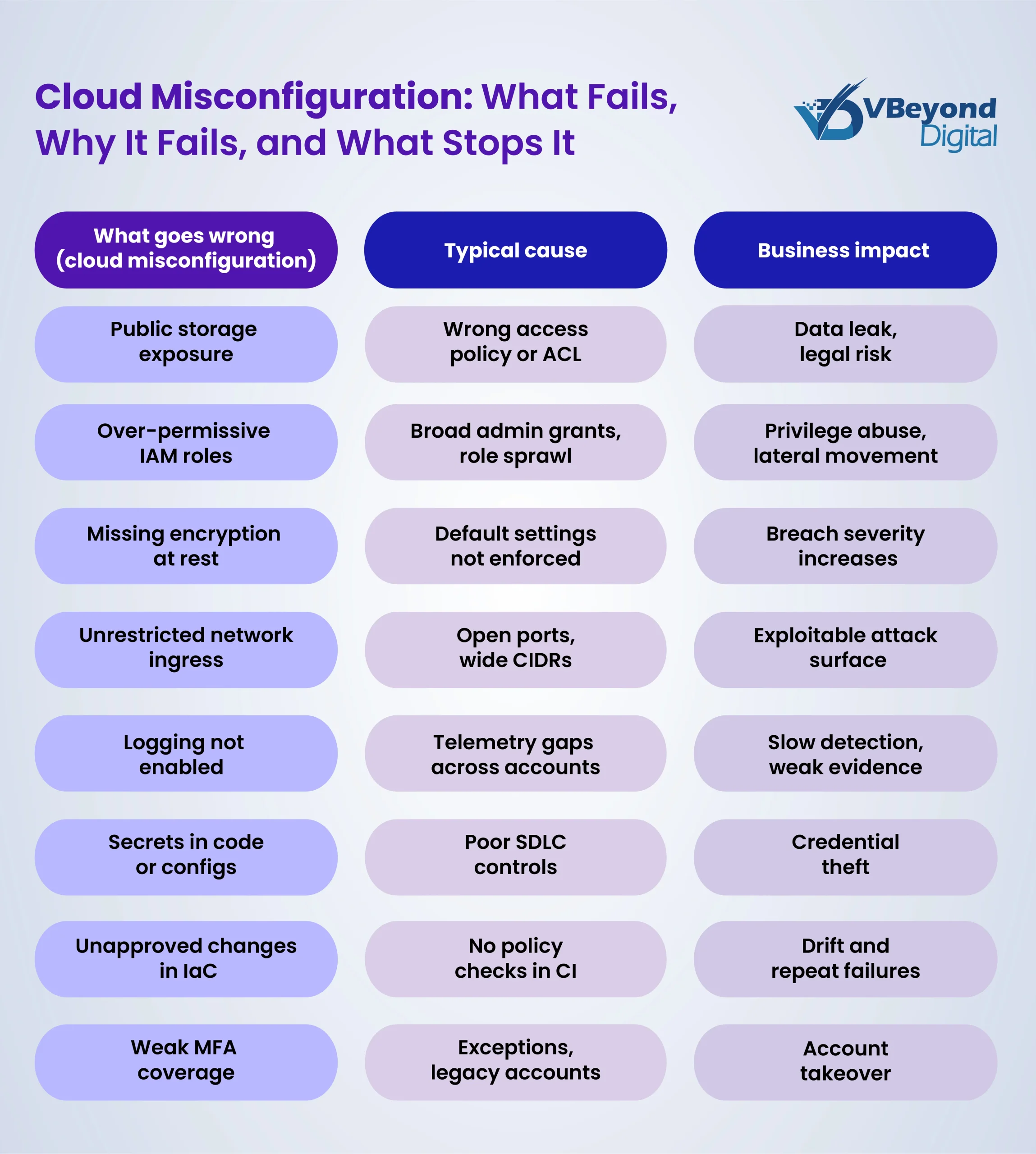
Misconfiguration can mean many things: forgetting to set a storage bucket to private, leaving default admin passwords in place, mismanaging network firewall rules, or not disabling unused access keys. These errors effectively leave the front door unlocked for attackers.
Such incidents are far too common. Industry research finds that misconfigurations or human errors are the root cause of roughly 31% of cloud data breaches, making it the single largest contributor. Even public sector organizations recognize this risk: as noted earlier, 88% of government agencies view cloud misconfiguration as their top security worry.
Why do misconfigurations happen so frequently in enterprise cloud environments? A few reasons are:
- Complexity and Scale: Large organizations have thousands of cloud assets (servers, databases, containers) and it is easy for settings to drift out of compliance. Tracking every configuration manually is nearly impossible.
- Cloud-Native Tools: Cloud providers offer dozens of security settings and identity roles. Misunderstanding a single setting (or forgetting to apply it uniformly) can open a hole. The shared responsibility model means cloud vendors secure the infrastructure, but customers must secure how they configure and use the cloud services.
- Fast-paced Changes: DevOps and Infrastructure-as-Code mean cloud environments change rapidly. Without automation or guardrails, new assets can be deployed with insecure defaults.
- Lack of Visibility: In multi-cloud setups, security teams may not have a single pane of glass. It is hard to get visibility into all configurations across AWS, Azure, GCP, etc., which means issues go unnoticed.
Impact: Cloud misconfiguration can lead to catastrophic breaches, regulatory penalties, and loss of customer trust. High-profile breaches like Capital One’s 2019 incident (exposing 100+ million records) were ultimately traced back to a misconfigured cloud resource.
Solution: The good news is that misconfiguration is preventable with the right practices and tools. Enterprises are increasingly adopting Cloud Security Posture Management (CSPM) solutions; these are automated tools that continuously scan cloud environments for misconfiguration and policy violations. They can alert teams to an open storage bucket or overly permissive identity role before an attacker finds it.
Another best practice is to follow industry benchmarks for secure configuration. Frameworks like the CIS Cloud Benchmarks (from the Center for Internet Security) provide consensus-based guidelines for securely configuring AWS, Azure, and Google Cloud services. Aligning your settings with CIS Benchmarks or similar standards can significantly reduce misconfiguration risks. Many organizations even automate compliance with these benchmarks as part of their DevOps pipelines, so that any new resource is checked against a secure baseline.
Meeting Cloud Security Compliance Standards
In highly regulated industries (finance, healthcare, government), and even for large enterprises in general, cloud security compliance standards are a major consideration. Companies must meet the same security and privacy requirements in the cloud as they do on-premises, if not more. This includes external regulations and internal policies around data protection, access control, incident response, and more. Some common cloud security compliance standards/frameworks enterprises may need to address include:
- Industry Regulations: For example, PCI DSS for payment data, HIPAA for healthcare data, GDPR for European personal data, or regulations like FedRAMP for U.S. government cloud usage. These all impose strict requirements on how cloud data is stored, used, and secured.
- Security Frameworks: For example, ISO/IEC 27001 (information security management), NIST CSF (Cybersecurity Framework), and SOC 2. While not cloud-specific, these frameworks guide overall security practices and are often applied to cloud environments to demonstrate strong controls.
- Cloud Provider Standards: For example, AWS Well-Architected Framework’s Security Pillar, Azure Security Benchmark, and Google Cloud’s security best practices. These are guidelines provided by cloud vendors to help customers maintain a secure and compliant architecture.
- CIS Cloud Benchmarks: As mentioned earlier, the CIS Benchmarks for cloud platforms (AWS, Azure, GCP) are widely used blueprints for baseline security configurations. Following these benchmarks can help meet many compliance controls (for example, ensuring encryption is enabled by default, or that logging is turned on for all critical services).
The challenge with compliance in a cloud context is twofold: understanding which standards apply and enforcing them continuously. In a hybrid or multi-cloud environment, different workloads might fall under different regulations. For instance, an enterprise might keep credit card processing systems in a private cloud to maintain PCI DSS scope, while using a public cloud for non-sensitive workloads. But data often flows between these environments, so consistent enforcement of policies is needed.
It is not easy; in fact, over half (54%) of organizations struggle to maintain consistent regulatory compliance across their hybrid and multi-cloud environments. This inconsistency can lead to gaps that auditors and attackers alike won’t miss. For example, you might have strong encryption enforced in AWS, but an Azure storage account is left unencrypted due to an oversight, violating compliance.
Strategies for Compliance: Achieving cloud compliance requires both process and technology:
- Unified Cloud Governance: Establish a cloud governance team or program that sets policies applicable across all environments. Define clear cloud security compliance standards that align with required regulations and frameworks. For example, mandate that all data classified as sensitive must be encrypted at rest, regardless of cloud platform or service used.
- Automated Compliance Monitoring: Leverage tools to continuously audit cloud configurations and deployments against your compliance requirements. Many CSPM tools and cloud provider services (like AWS Config, Azure Policy) can check resources against rules (e.g., “no publicly open S3 buckets” or “all databases must have encryption on”). Automation is key to catching non-compliance in real time.
- Regular Audits and Assessments: Schedule periodic audits (internal or third-party) of your cloud environment. These should include reviewing access controls, network security, data protection measures, and incident response plans for cloud workloads. Regular audits help identify drifts from compliance and demonstrate due diligence. In fact, companies that audit regularly are able to catch issues before they lead to incidents.
- Training and Awareness: Ensure that development and IT teams are trained on the compliance implications of cloud deployments. They should know, for instance, when a workload handles regulated data and what special steps are required in its cloud setup. A culture of security awareness helps prevent accidental compliance violations.
Cloud-Native Security Challenges (Containers, DevOps, and More)
Moving to the cloud often goes hand-in-hand with adopting cloud-native architectures. This means using microservices, containers, serverless functions, and continuous integration/continuous delivery (CI/CD) pipelines to rapidly build and deploy applications. Cloud-native technologies enable incredible speed and scalability, but they also introduce new security challenges that traditional security approaches may not cover.
Some cloud-native security challenges include:
- Ephemeral Infrastructure: In a cloud-native world, resources like containers or serverless functions are created and destroyed dynamically, sometimes within seconds. Traditional security tools that rely on fixed IP addresses or host-based agents can struggle to keep up with these short-lived entities. Ensuring every ephemeral instance is properly configured and scanned for vulnerabilities is difficult.
- Infrastructure as Code (IaC) Risks: Engineers now define cloud infrastructure (networks, servers, policies) as code templates (using tools like Terraform or CloudFormation). Mistakes in IaC templates can replicate misconfigurations at scale. A flawed template might deploy 100 vulnerable servers instead of one.
- DevOps Speed: The DevOps culture emphasizes rapid, frequent deployments. Security teams often find it challenging to insert checks without slowing down releases. There is pressure to avoid becoming a bottleneck, which can lead to security being skipped “just this once”, and that’s when issues slip in.
- Container and Kubernetes Security: Containers package applications and dependencies together, which is great for consistency, but vulnerabilities in the container image or in the orchestrator (like Kubernetes) have become a new attack vector. Misconfigured container networks or overly broad access in Kubernetes clusters can lead to breaches. Tools and expertise to secure these systems are still evolving.
The net effect is increased complexity. In fact, 41% of IT professionals say adopting cloud-native approaches (like microservices and containers) has increased complexity in their security operations. More moving parts mean more potential gaps if not managed carefully.
How can enterprises tackle cloud-native security? A few approaches are proving effective:
- DevSecOps Practices: This involves embedding security checks and tests directly into the CI/CD pipeline. For example, using automated scans of container images for known vulnerabilities before they are deployed, or running infrastructure-as-code through policy-as-code tools that flag insecure configurations. DevSecOps ensures security keeps pace with development.
- Container Security Platforms: Many organizations deploy container-specific security solutions that can do things like runtime container behavior monitoring, Kubernetes configuration auditing, and automated patching. These tools are akin to traditional endpoint protection but tailored to containers and cloud workloads.
- Micro-Segmentation and Zero Trust: Embracing a Zero Trust philosophy where no component is implicitly trusted because it’s inside the “cloud perimeter.” In practice, this means strong authentication between services, minimal network privileges (even between internal services), and encrypting data in transit. For example, each microservice might have its own credentials and only talk to the exact services it needs—if one service is compromised, it can’t freely attack others.
- Cloud-Native Visibility: Gaining visibility into cloud-native environments is crucial. Solutions like cloud workload protection (CWP) and observability tools (logging, tracing, metrics) help security teams know what “normal” looks like in a microservices environment, so they can detect anomalies. Because containers can spin up and down rapidly, having aggregated logs and monitoring is the only way to investigate incidents after the fact.
Hybrid Cloud Strategy: Balancing Security Across Private and Public Clouds
Most large enterprises run in a hybrid cloud model, a mix of a private cloud (or on-premises datacenter) and one or more public cloud services. This hybrid approach often emerges for good reasons: data sovereignty requirements, legacy systems that can’t easily move, or the need for ultra-low latency that only on-prem can provide. In fact, hybrid cloud is the dominant strategy today (as noted, about 73% of enterprises rely on hybrid cloud deployments).
However, a hybrid cloud strategy brings unique security considerations:
- Consistent Identity and Access Management: Users and systems might exist in two realms: on-prem Active Directory and cloud identity providers. Harmonizing these so that a user’s permissions are appropriate across both environments is tricky. Enterprises need solutions like single sign-on and centralized identity management that spans cloud and on-prem. A common problem is “permission creep” where, say, a developer has high privileges in the on-prem environment and also gets high privileges in the cloud, creating double the risk.
- Secure Connectivity: Data often travels between the private datacenter and public cloud (for replication, backup, or bursting workloads). Ensuring those connections (like VPNs or dedicated links) are encrypted and monitored is vital. Misconfiguring a hybrid connection could accidentally expose internal networks to the internet. Many enterprises use techniques like software-defined perimeters or secure SD-WAN to tightly control hybrid cloud network traffic.
- Data Placement and Encryption: Deciding which data lives on-prem vs. cloud affects security. Extremely sensitive data might remain in a private cloud segment with extra controls. But wherever data goes, encryption at rest and in transit should follow. Key management becomes complex when keys might reside in on-prem hardware security modules (HSMs) as well as cloud-based key management services. Leading organizations establish unified key management strategies so that encryption is consistently applied.
Unified Monitoring and Incident Response: It is inefficient and risky to have totally separate security monitoring for on-prem and cloud. Attackers won’t respect those boundaries; an incident might start in the cloud and pivot to on-prem resources or vice versa. Security operations centers (SOCs) need integrated Security Information and Event Management (SIEM) and incident response processes that cover the entire hybrid environment. This way, if an alert triggers in one environment, analysts can quickly assess if the other side is affected.
Best Practices for Hybrid Security:
- Clearly define data and workload placement: Develop criteria for what goes to public cloud vs private. For example, “Customer-identifiable data can only be stored on our private cloud segment unless approved by the security team” could be a policy. Classify data and map controls accordingly.
- Use consistent security platforms if possible: Many security vendors offer hybrid-cloud versions of their tools. For instance, a firewall vendor might have a virtual appliance for cloud that you can manage in the same console as your on-prem firewall. This consistency makes it easier to enforce uniform policies.
- Invest in cloud-skilled IT staff or partners: Managing hybrid security requires understanding both worlds. Ensure your team gets training on cloud security technologies. If the skills gap is too large (remember, 76% of organizations cite lack of skilled cloud security professionals), consider managed services or consulting partners to bridge the gap while upskilling your team.
- Plan for compliance across environments: As discussed earlier, ensure your compliance regime covers both sides. This might mean extending on-prem controls to cloud or vice versa. Auditors will look at the whole picture, so you should too.
- Regularly test incident response: Simulate breaches that jump from on-prem to cloud or vice versa. This will reveal any blind spots in logs, communication breakdowns between teams, or technical hurdles in investigating multi-environment incidents. Proactive testing is critical to being prepared.
Multi-Cloud Strategy: Managing Security in a Multi-Provider Environment
Many enterprises are not just hybrid, but truly multi-cloud, using two, three, or more public cloud providers concurrently. A multi-cloud strategy can be driven by a desire to use “best of breed” services (e.g., perhaps using Google’s AI platform, Azure for Office 365 integration, and AWS for core compute) or by M&A activity and different teams preferring different platforms. It can also be a deliberate tactic for resiliency and bargaining power. But how does an organization secure multi-cloud deployment effectively?
Challenges unique to multi-cloud:
- Diverse Security Controls: Each cloud has its own native security services and quirks. AWS has Security Groups, Azure has NSGs, Google Cloud has its Firewall rules, etc. Identity management differs (AWS IAM vs Azure AD roles vs GCP IAM). An admin must be fluent in each or risk misconfiguring one of them. When you multiply this across clouds, the chance of oversight increases.
- Tool Sprawl: Enterprises often end up using multiple security tools, some specific to each cloud’s ecosystem. For example, using AWS GuardDuty for threat detection in AWS, plus Azure Defender in Azure. If those tools don’t talk to each other, security findings can remain siloed. It’s harder to get a unified view of threats across all clouds.
- Network Complexity: Connecting multiple clouds (and possibly on-prem too) introduces network design complexity. Some companies build a multi-cloud network backbone or use third-party solutions to connect cloud environments securely. Mismanaging routing between clouds could inadvertently expose one cloud’s resources to another or to the internet.
- Inconsistent Policies: If one cloud environment is treated differently than another, gaps arise. For instance, perhaps you enforce strict multi-factor authentication for console access in AWS, but not in GCP, creating an easier target for attackers via GCP. Similarly, one cloud might have logging turned on by default while another doesn’t; inconsistent log policies can hinder incident investigations.
Strategies for Securing Multi-Cloud Environments:
- Abstract and Centralize: Many organizations opt for a cloud-agnostic security layer that sits above the individual clouds. This could be in the form of third-party solutions that integrate with all major clouds. Examples include centralized identity providers (federating each cloud’s accounts to one IdP), unified log management systems that ingest logs from all clouds, and CSPM tools that can scan multiple clouds against the same policies. By abstracting, you define a policy once (e.g., “no database should be publicly accessible”) and the tool checks it across AWS, Azure, GCP in their respective ways.
- Multi-Cloud Security Posture Management: As an extension of Cloud Security Posture Management (CSPM), some enterprises use Cloud Posture Management strategies specifically designed for multi-cloud. This involves defining a consistent set of security benchmarks (from CIS or internal standards) and using automation to apply and verify them in every cloud account. It also means getting a single dashboard that shows compliance and risk posture across all clouds, giving CISOs a high-level view of where the biggest risks are.
- Cross-Cloud Network Security: Simplify and secure connectivity by using encrypted tunnels or brokered connections between clouds. Treat inter-cloud traffic like external traffic: authenticate and encrypt it. Some advanced setups use a zero-trust network architecture even between their own cloud environments, verifying every connection.
- Leverage Cloud Provider Improvements: Recognize that the cloud providers themselves are aware of multi-cloud trends. They have started offering tools to help; for example, Azure Arc can manage servers across clouds, and Google’s Anthos or Azure’s upcoming multi-cloud management helps manage workloads in other clouds. While each provider wants to be primary, they know customers have choice. Keep an eye on these offerings but evaluate them carefully; they might introduce dependence on one provider’s ecosystem to manage others.
Don’t Forget Performance: Security and Cloud Performance Benchmarks
While the focus is rightly on security, enterprise tech leaders also care deeply about performance and user experience. A question that often arises: will our security measures hurt our cloud performance? It’s a valid concern—heavy encryption, deep packet inspection, or traffic hair-pinning through security appliances could introduce latency or throughput issues if not architected well.
Enterprises should strive for security without sacrificing performance. In fact, evaluating Cloud Performance Benchmarks across providers and configurations can guide decisions in a multi-cloud strategy. For example, Cisco’s ThousandEyes cloud performance report compared AWS, Azure, and GCP global network performance. It found that all three were generally consistent in performance, but each had regional variances—AWS showed less stability in certain regions (like Asia) compared to Azure and GCP. This kind of insight might influence how you distribute workloads (perhaps using Azure in a region where it has a known latency advantage).
The key point is that security and performance are not either/or. You can design an architecture that is both fast and secure:
- Use cloud-native security services where possible, as they are typically highly optimized (for example, cloud provider firewalls that operate at the hypervisor level can handle traffic with minimal latency).
- If using third-party security virtual appliances, ensure they are sized correctly and take advantage of autoscaling to handle load. And place them strategically, for instance, regional deployments to avoid backhauling traffic excessively.
- Regularly conduct cloud performance benchmarks of your own. Measure application response times with security features on vs. off (using test environments). This can uncover if a certain control, say an intrusion detection system, is adding 50ms of latency; then you can work on tuning it or consider alternatives.
- Take advantage of modern technologies like TLS offloading, content delivery networks (CDNs), and efficient load balancing to maintain performance even as you encrypt and inspect traffic.
Conclusion: Building a Secure and Agile Cloud Future
Enterprise cloud security is now a fundamental pillar of any digital strategy. The stakes are high: a single misconfiguration or compliance slip can lead to breaches that damage reputation and bottom line. Yet, with the right strategies, these risks can be managed. By addressing cloud misconfigurations, ensuring compliance across environments, tackling cloud-native security needs, and architecting strong hybrid/multi-cloud defenses, organizations can enjoy the full benefits of cloud agility safely.
In conclusion, enterprise cloud security is a journey, not a destination. Threats will keep evolving, and technologies will keep advancing. But by staying proactive, informed by data (as we’ve cited throughout), and outcome-oriented in our approach, we can navigate the challenges. The cloud can be a secure, compliant, high-performance home for even the most sensitive enterprise workloads, and with the right strategy, your organization can get there faster, with less risk.
FAQs (Frequently Asked Question)
Enterprise cloud security is the controls, processes, and tooling that protect data, identities, workloads, and networks in enterprise cloud computing. It covers prevention, detection, and response across public cloud, private cloud, and hybrid cloud strategy environments.
In 2026, enterprises will likely run more sensitive data and AI workloads across multi-cloud setups. This is expedted to increase exposure to cloud misconfiguration, identity abuse, and third-party risk. Enterprise Cloud Security protects revenue, uptime, and regulatory obligations while keeping delivery speed intact.
The biggest threats include cloud misconfiguration, overly permissive IAM roles, exposed storage or APIs, insecure CI/CD pipelines, weak secrets management, and visibility gaps from tool sprawl. Cloud-native security challenges in containers and Kubernetes also increase attack paths.
Standardize guardrails using policy-as-code, enforce MFA and least privilege, and adopt Cloud posture management across accounts and clouds. Add CI/CD checks for IaC and secrets, centralize logging, and measure remediation time. Treat security as a platform capability.
Compliance is tightening through more US state privacy requirements, stronger incident disclosure expectations, and updated security frameworks. Enterprises need audit-ready evidence generated from cloud telemetry, faster control mapping to cloud security compliance standards, and consistent enforcement across multi-cloud strategy environments.




