Azure Managed Services vs. Self-Managed: What SMBs Need to Know About Costs, Compliance & Performance
Section
Table of Contents
- Why This Decision Matters for SMBs
- What You’re Actually Choosing: Azure Managed Services vs Self-Managed Services
- Cost: Predictable vs. Variable
- Compliance and Risk: Shifting the Load, Not Dodging It
- Performance and Reliability: Results You Can Stand Behind
- Security: From Baseline to Proactive
- Conclusion
- FAQs (Frequently Asked Question)
- Managed vs. Self-Managed vs. Co-Managed: Managed delivers predictable outcomes and coverage; self-managed offers control but requires broad skills and 24×7 readiness; co-managed splits responsibilities to relieve pressure without losing ownership.
- Cost Reality: Model total cost over 12 months; include the cloud bill, people time, and an incident and audit reserve; use tags, budgets, and reservations to keep spend steady.
- Compliance and Risk: Azure secures the platform; you and your partner secure configuration and operations; make evidence part of daily work with access reviews, change logs, and backup tests.
- Performance and Reliability: Design for resilience first; define SLOs that map to business impact; practice recovery and record results so confidence is defensible.
For most SMBs, cloud is no longer a leap; it is the default way to get modern apps, scale on demand, and pay for what you use. Within that landscape, Azure is a natural anchor given its enterprise security, Microsoft ecosystem, and global footprint. The real differentiator now is not whether you choose Azure; it is how you run it. The right operating model yields steady gains, while the wrong one can turn into an expensive mistake.
Think of this choice as an operating blueprint rather than a tool checklist. Managed Services shift day-to-day operations to a partner with clear outcomes, while a self-managed approach keeps control in house and asks your team to carry the full weight of architecture, on-call, and audit readiness. A co-managed model is somewhere in the middle, letting you keep ownership where it matters and bringing in help where you lack time or depth.
If you are a founder or IT leader who values predictability, or a technical lead who wants a defensible path to stronger uptime and lower risk, this blog is for you. By the end, you will have a simple scoring rubric, a short list of questions to ask any provider, and two reference setups you can adapt to your environment.
Why This Decision Matters for SMBs
The operating model you choose shapes real outcomes. It affects how predictable your expenses feel each month, how quickly you recover from issues, and how confident you are when customers or auditors ask tough questions.
Most SMBs face a similar set of triggers. Growth creates more apps and more environments to watch. A security scare or a near miss pushes you to tighten controls. A new customer or regulation raises the bar for evidence. Budget pressure forces a closer look at the human time behind every alert and change request.
What “good” looks like is straightforward. The right model for your enterprise means fewer surprises, clear ownership, shorter recovery when things go wrong, and simple reports that a nontechnical leader can understand. You get there by treating operations as a business process, not a hero effort. That means a cadence for reviews, named owners for cost and risk, and a small set of service levels you can meet.
Below are a few practical anchors that can help you stay on track:
- Connect spending to teams so you can see who drives costs (use Azure cost tags and budgets).
- Make monitoring useful, not noisy (collect metrics and alerts that map to customer impact).
- Practice recovery on a schedule, so confidence is earned, not assumed (backup tests and basic failover drills).
- Keep an audit trail that is easy to produce when asked (change logs and access reviews).
There are people factors too. Small teams can burn out overnight support. Hiring and training take time to go to product work. The right model gives you a breathing room while keeping control where you want it.
Make Azure Operations Predictable Today
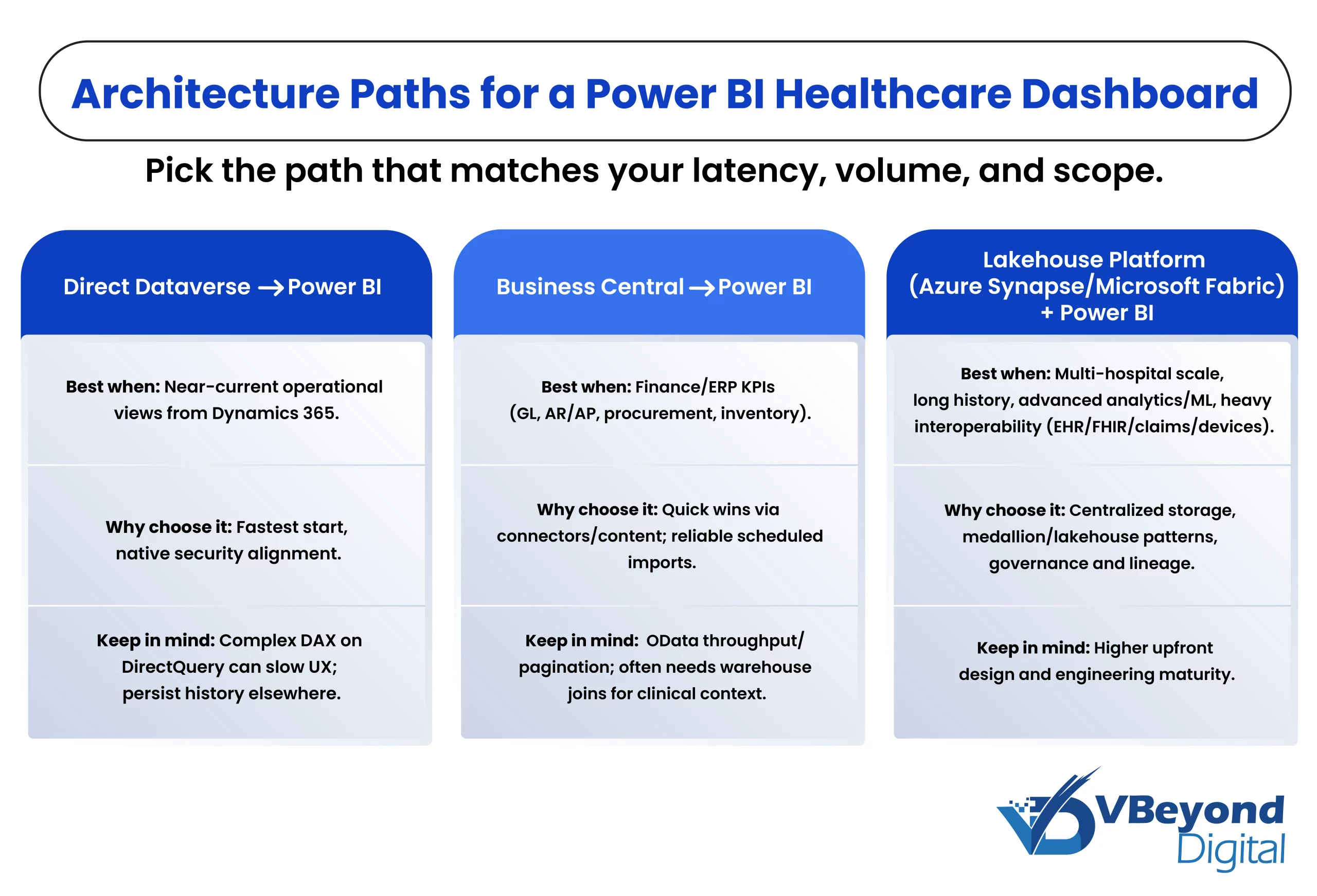
What You’re Actually Choosing: Azure Managed Services vs Self-Managed Services
Once you pick Azure, the real decision is how you will run it day to day. You are choosing where responsibility sits, how predictable your costs will be, and how resilient your operations feel when things go wrong.
Managed Services on Azure
Managed Services shift operations to a partner with defined outcomes. You get a named contact, service levels, and a consistent cadence for reviews. The provider watches your cloud environments around the clock, handles routine patching and backups, and brings playbooks for common incidents. In practice, this feels like buying stability and time.
A good partner will identify improvements and suggest recommendations, then implement agreed changes inside a clear change window. Expect light technical touchpoints that move the business forward, such as quarterly rightsizing, security posture reviews, and recovery drills.
To evaluate an Azure managed service provider, ask how they use cost tagging and budgets, how they tune alerts to reduce noise, and how they test RTO and RPO for your top workloads.
Self-Managed on Azure
Self-managed keeps control in house. Your team designs the architecture, runs the pipelines, tunes performance, and carries the pager. This model suits teams that already have the breadth to cover networking, identity, security, data, and cost control, or that want to build those muscles.
The upside is direct control and faster experimentation. The tradeoff is the ongoing investment in people, training, and process. Plan for on-call coverage, documentation, and a simple governance rhythm so the work scales with the business.
Co-Managed as a Practical Middle Ground
Co-managed splits responsibilities. You keep ownership of what differentiates your business and bring in a partner where you want reliability and scale. Common splits include letting a provider run monitoring, patching, backup checks, and first response, while your team owns architecture and product changes.
This approach works well when you need breathing room but do not want to give up control. It also creates a path for mentoring, where the partner helps upskill your team over time.
Cost: Predictable vs. Variable
Cost is not only what Azure charges. It is also the people’s time, the process overhead, and the price you pay when things go wrong. A useful comparison looks at three buckets: the cloud bill, the operating team, and the hidden or indirect costs.
The Cloud Bill
You pay for compute, storage, networking, and data movement. Two teams can run the same app and get very different bills based on sizing and schedules.
- Rightsize and schedule: Match instance size to real demand; shut down nonproduction at night and on weekends.
- Use commitments wisely: Reserved Instances and Savings Plans reduce unit rates when usage is steady. Start small and expand.
- Watch data movement: Egress, cross-region traffic, and chatty services add up. Place dependent services close together and cache aggressively.
- Tag and budget: Tag by team, app, and environment. Create monthly budgets with alerts before you overshoot.
People and Process
Self-managed means salaries, on-call, training, and the time leaders spend in reviews. Managed services mean a monthly fee with a defined scope.
- Self-managed input: At minimum, plan for 1 to 3 FTEs to cover operations, security basics, and cost control. Include training and certification refresh.
- Managed input: Retainer tiers vary by size and scope. Ask what is included by default and what requires a change request.
- Governance rhythm: Set a monthly review for cost, security posture, and performance. Keep it to one hour with a clear action list.
Hidden and Indirect Costs
These are the costs that surface only when stress hits. Plan for them up front so they do not surprise you later.
- Downtime and slowdowns: Lost revenue, SLA credits, and reputation damage. Even short incidents can ripple.
- Security remediation: Cleanup, investigations, and potential legal or customer obligations.
- Audit preparation: Hours spent assembling evidence if you do not collect it as you go.
- Tech debt: Manual steps and fragile scripts that slow every change.
How To Compare Apples to Apples
Create a 12-month TCO view with three scenarios: self-managed, managed, and co-managed. Include the cloud bill, people and process, and a small reserve for incident and audit time.
- Inputs to model: average monthly compute and storage, expected growth percent, on-call coverage hours, training budget, managed service fee, and an incident reserve.
- Sensitivity test: Vary usage by plus or minus 20 percent and include one moderate incident. See how each model handles volatility.
- Contract clarity: For managed services, list what is included, what is out of scope, and how change requests are priced.
Compliance and Risk: Shifting the Load, Not Dodging It
Compliance is not a one-time project. It is a routine that proves your controls work. The question is who carries which parts of that routine and how easy it is to show evidence when asked.
Understand the Shared Responsibility Model
Azure provides secure infrastructure, regional controls, and platform assurances. You and your partner configure how your workloads use that platform. That includes identity and access, network policy, data protection, logging, and backup and recovery. In a managed model, the provider performs many of these tasks under your direction. In a self-managed model, your team owns them end to end.
Focus on the Frameworks That Matter
Most SMBs see some mix of ISO 27001, SOC 2, GDPR, HIPAA, or PCI. Do not try to do everything at once. Map your business to the few controls that actually drive customer trust and legal obligation. Start with identity, change control, backup testing, and incident response. Add data retention and encryption specifics as your industry requires.
Make Evidence Collection Part of Daily Work
Audits go smoothly when evidence appears without a scramble. Build small habits into operations so proof is produced as a byproduct.
- Run access reviews on a schedule and store the sign-offs.
- Record changes with tickets and link them to automated pipelines where possible.
- Keep backup and restore results in a simple log with screenshots or console outputs.
- Store security findings and their remediation notes in one place.
Clarify Who Owns Risk and Response
Incidents test accountability. Write down who triages, who communicates, who decides on containment, and who talks to customers. In a managed or co-managed model, specify the boundary between first response and deeper remediation. In a self-managed model, make sure on-call rotations and escalation paths are clear and humane.
Contract Essentials with a Managed Partner
Contracts should make compliance easier, not harder. Ask for plain language and measurable commitments, with some of the essential activities including:
- Clear and transparent data handling and processor obligations
- Notification windows for security events
- RTO and RPO targets by workload, with proof of testing
- Scope that lists what is included by default and what requires a change request
- Exit and knowledge transfer terms so you can move providers without losing control
Performance and Reliability: Results You Can Stand Behind
Performance needs speed, not just for the sake of it, but to deliver a steady experience that matches what customers and leaders expect. Reliability is your ability to keep that experience intact under normal load and during stress.
Design for Resilience Before You Tune for Speed
Start by removing single points of failure. Use multiple availability zones for critical workloads. Place dependent services in the same region to reduce latency. Add caching near users and at the data layer to smooth spikes. Build autoscaling policies so capacity grows and shrinks with demand.
Measure What Matters to the Business
Choose a small set of indicators that map to user impact. Uptime, response time at the 95th percentile, and error rate are easier to defend in a board meeting than a dozen internal metrics. Track alert volume as a quality signal. Fewer, clearer alerts mean your team can act faster.
Set Recovery Targets by Workload
Not every system needs the same protection. Define recovery time objective and recovery point objective for each major workload. Customer-facing systems usually need tight targets. Internal analytics may tolerate longer recovery if backups and data freshness are clear.
Create a simple matrix with three to five workloads. List RTO, RPO, owner, and the last time you tested recovery. Review it in your monthly governance meeting.
Practice Recovery So Confidence Is Earned
Run backup restores a lightweight failover drill on a schedule. Capture start time, end time, and issues found. Treat every drill as a learning loop. Update runbooks, tune alerts, and record evidence so you can show progress.
Keep Operations Calm During Incidents
When an incident happens, clarity beats speed. Write down who triages, who communicates, and who decides when to roll back or fail over. Get customer messaging templates ready. After the event, perform a short review that identifies a few corrective actions with owners and dates.
Security: From Baseline to Proactive
Security should feel routine, not reactive. Aim for a strong foundation first, then add practices that find and fix issues before they matter.
Establish a Strong Baseline
Set simple, universal controls that lower risk across every environment.
- Identity first: Enforce multifactor authentications for all users, require Conditional Access for admins and sensitive apps, and remove standing global admin rights.
- Least privilege: Define roles by task, review access on a schedule, and require approvals for elevation.
- Patch and harden: Keep operating systems and runtimes current, turn on automatic updates where safe, and lock down remote access.
- Protect data: Encrypt at rest and in transit, inventory sensitive data, and restrict where it can live.
- Centralize logs: Send platform, application, and security logs to one workspace with retention that meets your obligations.
Move to Proactive Practices
Once the floor is set, add habits that surface weak spots early.
- Threat detection you can read: Tune alerts to reflect real risk, not noise. Focus on account compromise, unusual data movement, and exposed services.
- Vulnerability management with follow through: Scan regularly, assign owners, and set clear timelines for remediation. Track exceptions and revisit them.
- Secrets and keys under control: Store secrets in a secure vault, rotate keys, and remove secrets from code and pipelines.
- Secure development habits: Require code reviews, run dependency checks, and add lightweight security tests to CI.
- Tabletop and drill cadence: Practice incident response with short tabletop sessions, then run one technical drill per quarter.
Clarify Roles and Handoffs
Security work crosses teams. Write down who owns identity, who owns network policy, who triages security alerts, and who approves containment steps. In a managed or co-managed model, be explicit about first response, escalation, and customer communication.
Keep Evidence Easy
Make proof a byproduct of normal work.
- Store access review results with signoffs.
- Keep vulnerability reports and closure notes together.
- Save incident timelines, post-incident actions, and due dates.
- Record backups restore outcomes and dates.
Signals That Your Posture Is Improving
- Critical vulnerabilities trend down and stay down.
- Mean time to acknowledge and mean time to recover improve quarter over quarter.
- Fewer false positives, clearer alert descriptions, and faster decisions.
- Auditors get what they need without scrambling.
Conclusion
Operating on Azure is less about tools and more about clarity. Choose the model that matches your team’s capacity and your risk profile, then make it routine. Keep costs visible with tags and budgets. Set a small set of service levels that leaders can understand. Practice recovery so confidence is earned. Treat compliance as evidence you produce as part of normal work, not a separate project.
If you prefer steadier costs, consistent coverage, and faster recovery, a managed or co-managed approach is often the safer path. If you have the people and the appetite to build operational muscle, self-managed can work well with strong guardrails. In either case, a predictable cadence wins: monthly reviews, clear owners, and a short list of actions that actually move the needle.
FAQs (Frequently Asked Question)
Managed shifts day-to-day operations to a partner with SLAs, 24×7 monitoring, patching, backups, and regular reviews. Self-managed keeps full control in-house but demands broad skills, on-call coverage, governance, and training. Co-managed splits responsibilities to relieve pressure without losing ownership.
Azure Managed Services outsources operations to a named partner delivering defined outcomes: 24×7 monitoring, patching, backups, tuned alerts, and quarterly improvements. Self-managed Azure means your team designs, runs, and supports everything—architecture, pipelines, cost control, security, and audit evidence.
Often, yes—when you value predictability, audit readiness, and 24×7 coverage. Compare via a 12-month TCO: cloud bill + people/process + incident/audit reserve. Managed is a fixed retainer; self-managed may require 1–3 FTEs plus training and on-call.
Azure secures the platform. You and the provider secure configuration and operations: identity and access, network policy, data protection, logging, and backup/recovery. Define RACI, incident handoffs, and RTO/RPO per workload, and require tested evidence as part of routine work.
Seek proof of cost governance (tags, budgets, RI/Savings Plans), alert noise reduction, and regular recovery testing with RTO/RPO by workload. Clarify scope vs change requests, SLAs and escalation, data-handling and breach notifications, and exit/knowledge-transfer terms. Prefer quarterly reviews and named contacts.




