Least-Privilege Azure: Tackling RBAC Wildcards to Secure BI Environments
Section
Table of Contents
- Why are BI Environments Vulnerable to Wildcards?
- What’s Changing in Microsoft Fabric & Power BI?
- Common Problem Scenarios and Their Solutions
- Examples of Mapping Roles for Microsoft Fabric and Power BI
- A 90-day Timeline to Securing Your BI Environment
- Conclusion: Partner with VBeyond Digital to Secure Your BI systems
- FAQs (Frequently Asked Question)
- Purpose and scope: Why wildcard permissions in Azure RBAC create lateral movement in BI workspaces and how control plane and data plane permissions interact. The blog explains the mechanics of Actions, DataActions, NotActions, and NotDataActions, and references research findings on wildcard risk.
- What is changing: The Microsoft Fabric security updates for 2025, including removal of the default Contributor grant for Fabric Workspace Identity and workspace access limits. It also clarifies Power BI role-based access and how to use Admin, Member, Contributor, and Viewer with group assignments.
- How to fix it: A practical model for Azure least privilege using Custom Azure roles without wildcards, time-bound access through PIM, and recurring Azure Access Reviews. It includes role mapping examples for service principals, analysts, and operations, aligned with Power BI Security.
- Guardrails and outcomes: Pre-commit linting to flag wildcards, use of built-in deny assignments where present, monthly drift reporting, and a 90-day execution plan. Leaders get faster approvals, smaller access radius, clear ownership, and audit-ready evidence that aligns with Azure RBAC best practices and Microsoft Fabric security.
In shared BI workspaces, broad Azure RBAC (Role-Based Access Control) assignments can enable lateral movement paths that auditors will flag, and attackers can exploit. The shortest path to a safer BI estate is explicit permissions backed by time-bound elevation. While seemingly convenient, wildcards pose a security risk. Recent academic analysis shows that ill-placed wildcards, including infix patterns, can widen reach across resource providers.
Why are BI Environments Vulnerable to Wildcards?
Business intelligence is an area of reporting where analysts, pipelines, and operations collide. That mix creates several choke points where a single wildcard can overreach.
Where It Happens
- Control plane: Broad Azure RBAC assignments at management group, subscription, or resource group scope flow into every Fabric workspace that lives there. In Power BI, workspace roles such as Admin, Member, Contributor, and Viewer control who can publish or change content.
- Data plane: DataActions govern read and write against data itself, for example storage, Lakehouse or OneLake items, and SQL endpoints. These are separate from control plane Actions and are evaluated to allow operations on data.
Patterns That Create Risk
- Assigning Contributor roles widely so teams can publish quickly gives create, edit, and delete capabilities across workspace content. That is helpful in the short term but expands write paths that auditors will question.
- Building Custom Azure roles with patterns like Microsoft.*/* (a giant wildcard in Azure RBAC role definitions) or using NotActions to subtract a few items from a broad grant. Microsoft documents that NotActions subtracts from allowed Actions and is not a deny. In fact, deny assignments are processed separately.
- Depending on built-in roles without validating scope or effective permissions. Recent research has identified over-privileged Azure built-in roles, which raises the stakes when those roles are used broadly in BI estates.
Safeguard BI Against Wildcards
What’s Changing in Microsoft Fabric & Power BI?
Microsoft Fabric security is tightening. Starting July 27, 2025, the default Contributor assignment for Fabric Workspace Identity is removed. New and existing Workspace Identities will no longer receive Contributor automatically. This reduces unintended write access from service identities and aligns with Azure least privilege goals. Plan to explicitly grant roles only where required.
Microsoft has already begun updating and enforcing access limits. Fabric workspaces will enforce a permanent limit of 1,000 users or groups assigned to workspace roles during a rollout window between August 1 and August 31, 2025. This change targets stability and access hygiene. Capacity and workspace owners should consolidate role assignments and rely on groups where practical.
Power BI role-based access remains the operating model. The supported workspace roles are Admin, Member, Contributor, and Viewer. Assign these to individuals or to security groups rather than using broad direct grants. This lets you keep delivery speed while narrowing who can publish or change content.
Practical implications for Azure RBAC and Azure role-based access control in BI:
- Map analysts to Viewer or Member to separate authoring from administrative control. Restrict publishing and overwrite to a small set of service principals.
- Move Workspace Identities off default write paths. Grant only the specific permissions their connectors and pipelines need.
- Use Azure Access Reviews to right-size workspace and group membership on a recurring cadence, especially as the 1,000-assignment limit comes into effect.
Common Problem Scenarios and Their Solutions
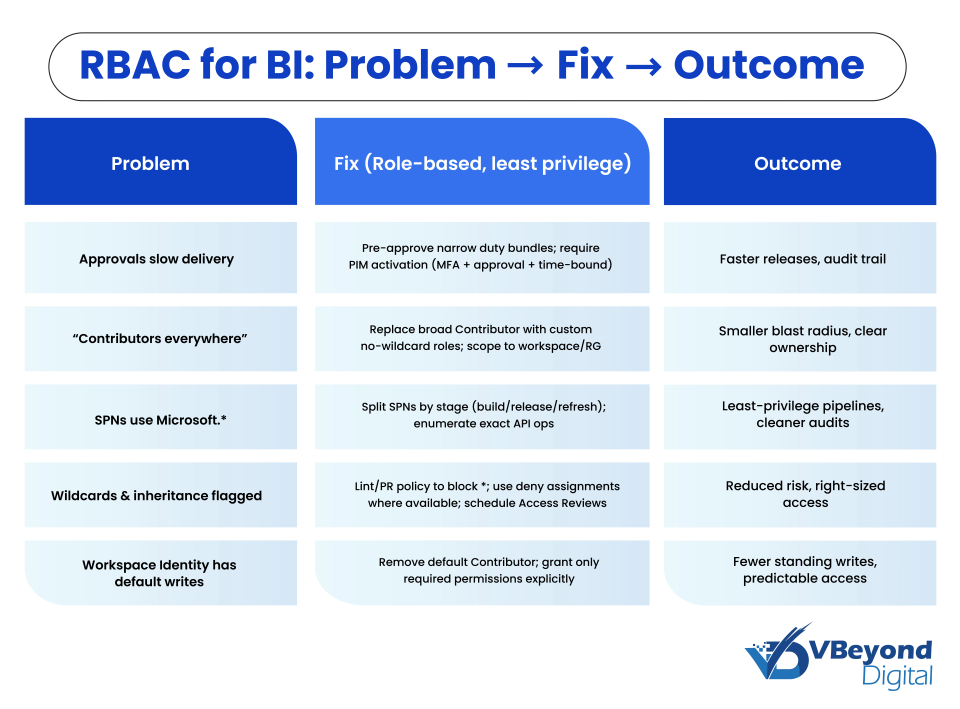
Problem: “We need rapid BI delivery, but security approvals stall.”
Solution: Preapprove narrow duty bundles that align to Azure least privilege. Examples include publish, refresh, share, and pipeline run. Make users eligible for these roles and require activation through Microsoft Entra PIM with approvals, MFA at activation, and time limits. This reduces standing privilege and shortens approval cycles while keeping evidence for audits.
Problem: “Contributors everywhere. No one knows who can overwrite datasets.”
Solution: Replace broad Contributor with Custom Azure roles that enumerate exact Actions and DataActions. Avoid the “*” wildcard and list required operations, so permission scope does not expand when new provider Actions appear. Scope assignments to the specific workspace or resource group.
Problem: “Service principals use Microsoft./ for automation.”
Solution: Split automation by stage. Use separate service principals for build, release, and refresh. For each principal, list only the API operations the pipeline needs instead of Microsoft./. This pattern prevents accidental writes across providers and supports clean audit trails in Azure RBAC. Pair with PIM eligibility for just-in-time activation.
Problem: “Audits flag wildcard grants and risky inheritance.”
Solution: Add guardrails. Use policy and code review to block wildcards in Custom Azure roles and prefer explicit permissions. Where stronger control is required, remember that NotActions is not a deny. Deny assignments can block access even if a role appears to allow it, and they are managed by Azure. Align this with Azure Access Reviews to right-size group and workspace membership on a schedule.
Outcome: Faster approvals, smaller access radius, and audit-ready evidence that aligns with Azure RBAC best practices and Power BI role-based access while maintaining delivery speed for BI teams.
Examples of Mapping Roles for Microsoft Fabric and Power BI
CI/CD publishing service principal
- Control plane: Assign the service principal only to the target workspace and only with the role that allows publishing tasks. Power BI workspace roles are Admin, Member, Contributor, and Viewer. Use the narrowest role that supports your deployment flow and assign it to a security group wherever possible.
- Pipeline automation: Deployment pipelines support service principal authentication. Use a dedicated Entra application for the pipeline connection and enable service principal access in tenant settings before use.
- Data plane: Grant only the storage or SQL permissions that the pipeline needs to refresh or write metadata. Fabric Workspace Identity can be used by items such as Dataflows Gen2 and pipelines to authenticate to Azure resources through Microsoft Entra. Keep writing minimal and prefer to read where possible.
- Time bound: Make the principal eligible in Microsoft Entra Privileged Identity Management and require activation with approval and MFA for sensitive stages. This follows Azure RBAC best practices for just-in-time access.
Analyst persona
- Map day-to-day analysts to a Viewer role when they only need to read workspace content. Use Member role for authoring without full administrative rights. Keep publish and overwrite reserved for specific service principals or a small engineering group.
Operations persona
- Grant read permission across workspaces for monitoring and incident review. Permit temporary elevation for fixes through PIM, with recurring Azure Access Reviews to keep group and role membership current.
Fabric Workspace Identity shift
- Microsoft Fabric will remove the default Contributor assignment for Workspace Identity effective July 27, 2025. Plan explicit role grants that reflect the identity’s actual tasks, such as connectors and Dataflow Gen2 operations. Pair this with your Azure RBAC scopes and group assignments.
A 90-day Timeline to Securing Your BI Environment
Week 2: Complete an inventory of wildcard usage across Actions and DataActions. Produce a heatmap of high-impact identities and BI workspaces. Prioritize items with “*” in Custom Azure roles and any broad Contributor assignments in Azure RBAC.
Week 4: Move the first duty-based roles into non-production. Split pipeline service principles by stage and list required operations explicitly. Validate Power BI role-based access by assigning Admin, Member, Contributor, or Viewer only where needed.
Week 6: Turn on Microsoft Entra PIM for high-impact roles with approval, MFA at activation, justification, and time limits. Begin recurring Azure Access Reviews for key groups tied to BI workspaces.
Week 12: Establish a no-wildcard baseline for BI. Align Fabric Workspace Identity with the removal of default Contributor and prepare for workspace access limits. Document the process as part of setting Azure RBAC best practices and Power BI Security routines.
Outcome: Tighter Azure role-based access control, faster approvals, fewer standing writes, and clean audit evidence that scales across Microsoft Fabric security and Power BI environments.
Conclusion: Partner with VBeyond Digital to Secure Your BI systems
We bring clarity and velocity to access control so BI teams can ship without broad grants. Our approach starts with clear duties, explicit permissions, and measurable controls that align with Azure RBAC and Azure RBAC best practices. We design Custom Azure roles that avoid wildcards, set up time-bound activation, and build review rhythms that your leaders can trust.
From strategy to build, we help tech leaders turn transformation into measurable outcomes. That includes practical guidance on Power BI role-based access, Microsoft Fabric security configuration, and Fabric Workspace Identity changes. We align group models with Azure role-based access control, put Azure Access Reviews on a predictable cadence, and maintain clean evidence that supports audits.
Whether you are modernizing infrastructure or building a digital-first product team, we help you get there faster with less risk. The result is a safer path to delivery, stronger Power BI Security controls, and a platform that scales through clear ownership and repeatable governance.
FAQs (Frequently Asked Question)
Wildcard permissions and broad Contributor grants. A “*” in Actions or DataActions can expand across providers as new operations appear. NotActions only subtracts from what is granted and is not a denial. In BI, this creates overwrite, export, and lateral movement risk across workspaces.
Use explicit permissions in Custom Azure rules and avoid *. Limit the scope of access to the smallest viable workspace or resource group. Assign rights to groups, not individuals. Add just-in-time access with Entra PIM and schedule Azure Access Reviews. Keep publish rights narrow with Power BI role-based access.
Default Contributor for Fabric Workspace Identity is removed on July 27, 2025. Workspaces also enforce a limit of 1,000 users or groups per role assignment during August 2025. Plan group-based assignments, redesign Contributor usage, and map duties to precise permissions that match Azure RBAC goals.
Mobile access follows Power BI workspace roles and app permissions. If a user has Viewer or app access, they can open reports. Azure RBAC influences backend access when Fabric items or connectors call Azure services through Fabric Workspace Identity. Missing data permissions can cause visual or refresh failures.
Use Microsoft Entra Permissions Management to analyze permission usage, highlight excessive rights with the Permission Creep Index, and recommend right-sizing. Pair it with Entra PIM for time-bound activation and audit trails. This combination reduces standing privilege while keeping Azure RBAC aligned to least privilege.




